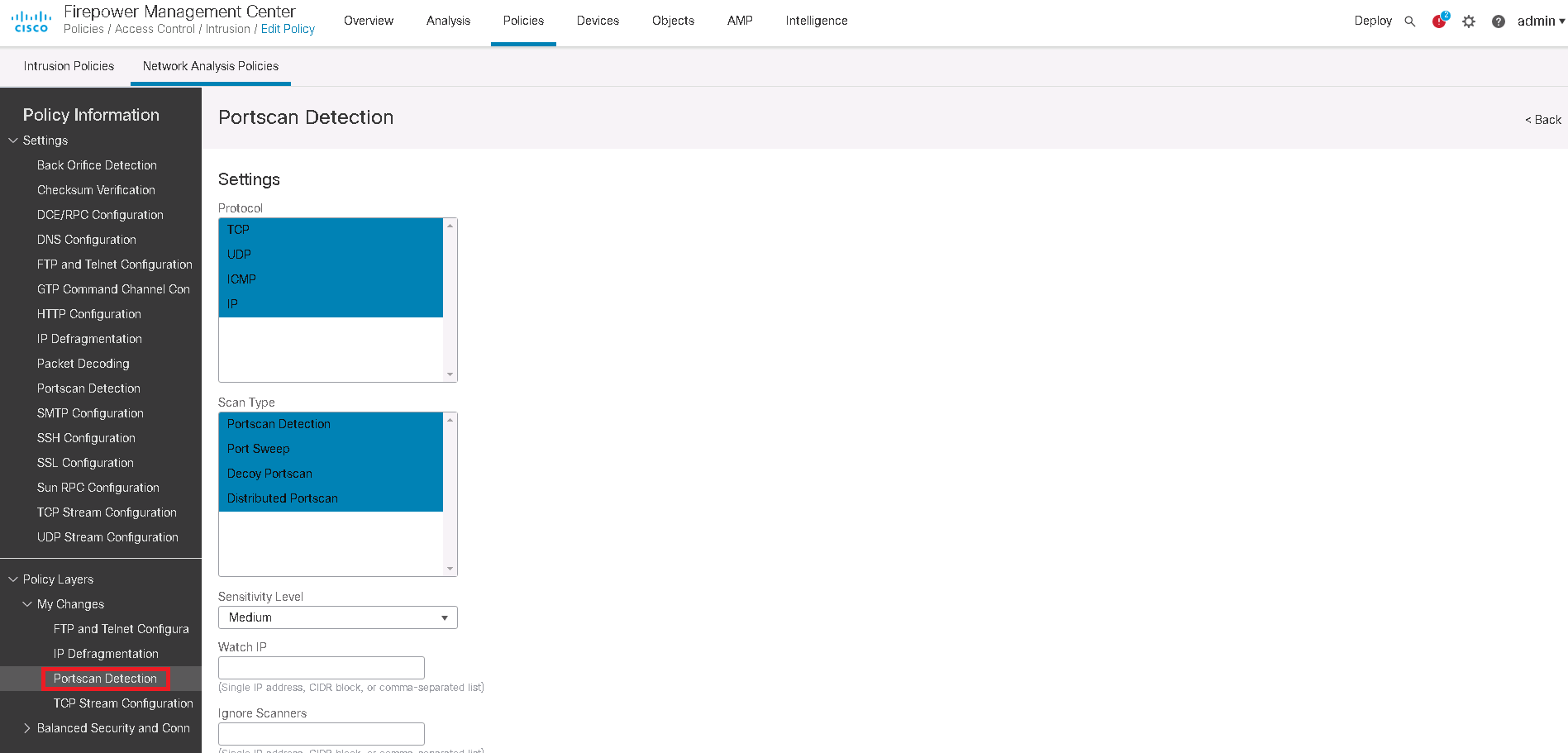
A proposal of port scan detection method based on Packet‐In Messages in OpenFlow networks and its evaluation - Ono - 2021 - International Journal of Network Management - Wiley Online Library
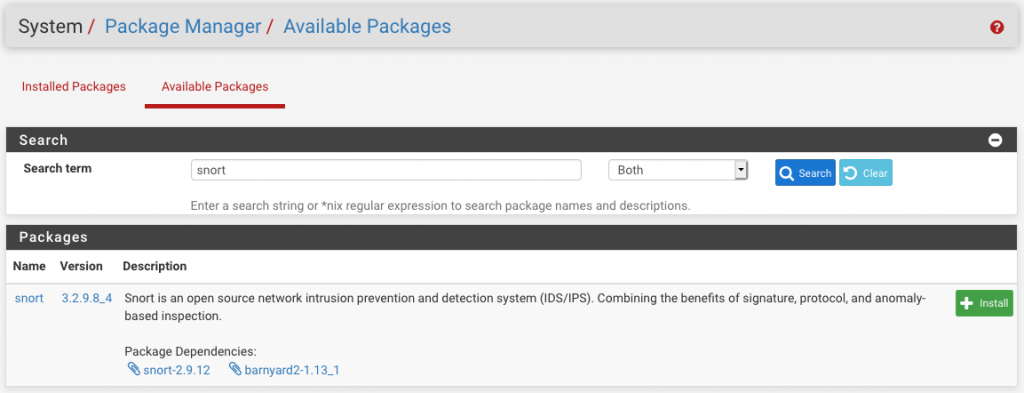
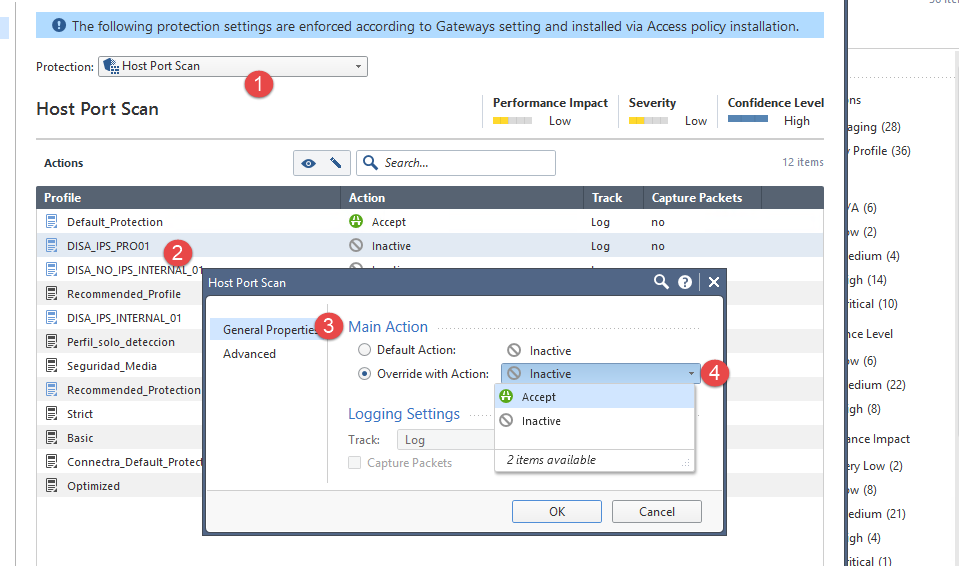
Automatically Detect and Block Port Scanning With pfSense and Snort | Linux & Cybersecurity in Australia
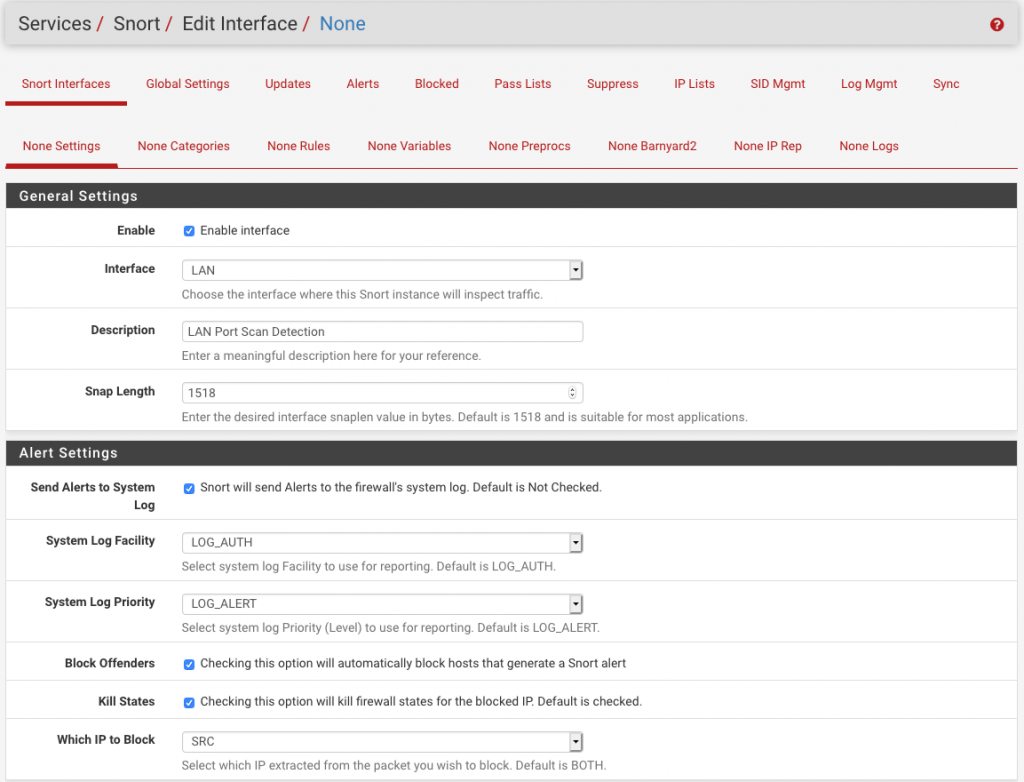
Automatically Detect and Block Port Scanning With pfSense and Snort | Linux & Cybersecurity in Australia
![PDF] Alternative Engine to Detect and Block Port Scan Attacks using Virtual Network Environments | Semantic Scholar PDF] Alternative Engine to Detect and Block Port Scan Attacks using Virtual Network Environments | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1b227ea0f684755183d7c36873c00a853f2e9f73/6-Figure3-1.png)



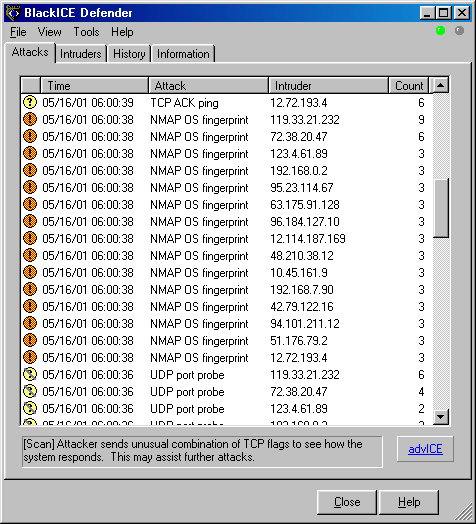
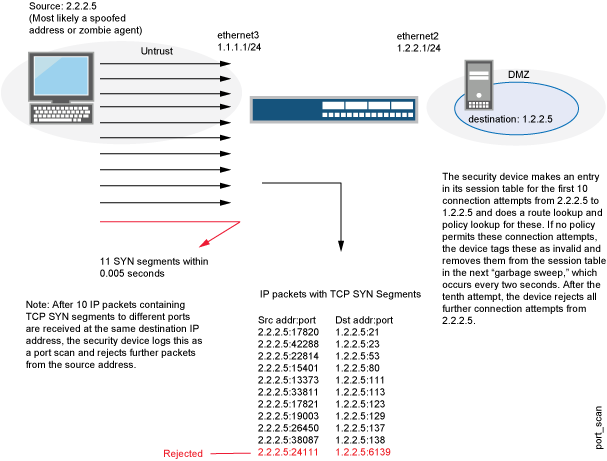
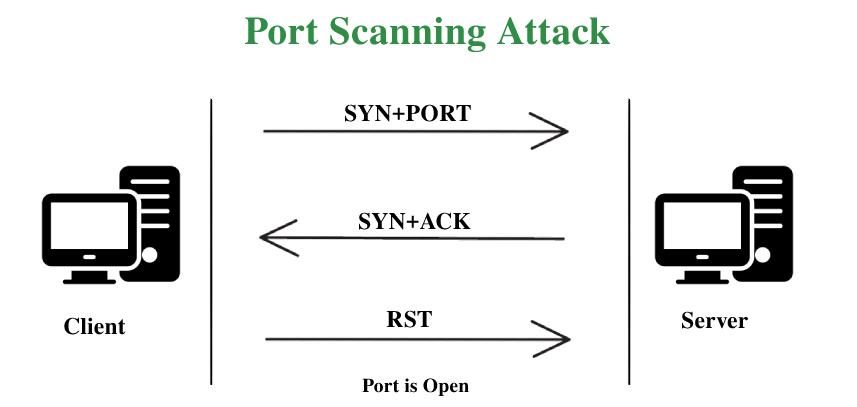

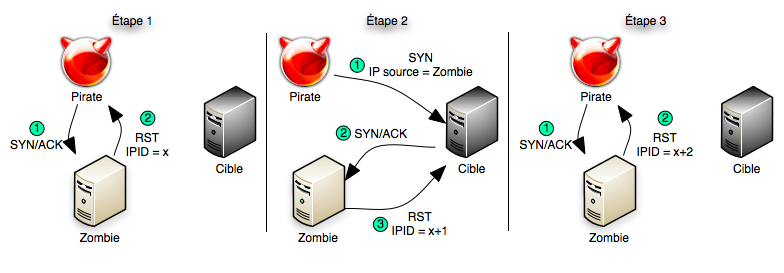
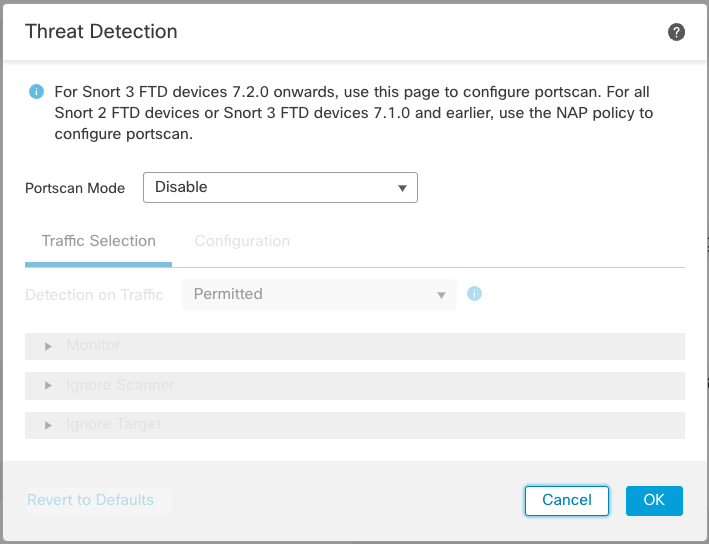


![KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x–16.x) KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x–16.x)](https://support.eset.com/storage/IMAGES/en/KB2951/KB2951Fig1-1e.png)
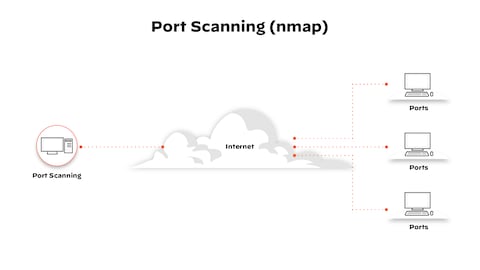
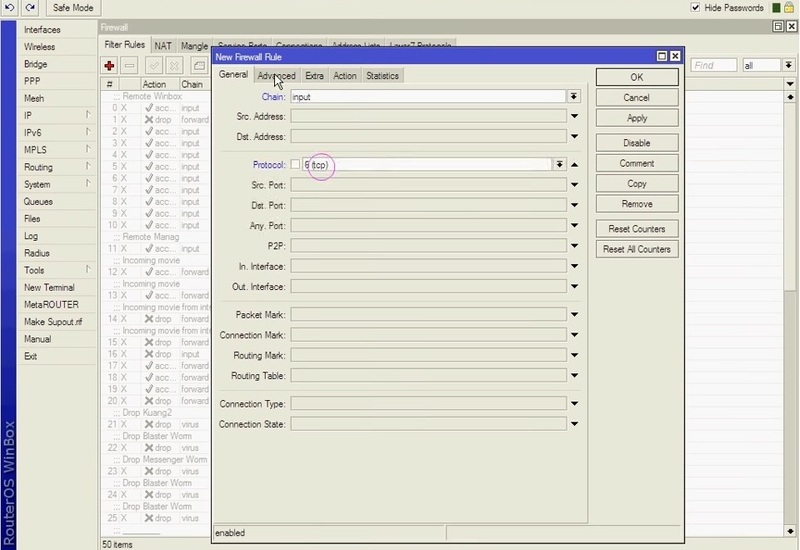
![How to block port scanner in MikroTik [Prevent Port Scanning] How to block port scanner in MikroTik [Prevent Port Scanning]](https://monovm.com/uploads/tinymce/Block%20port%20scanner%20on%20mikrotik/3.webp)